
 BTC $105279
BTC $105279 LTC $85.331
LTC $85.331 SOL $144.383
SOL $144.383 DASH $19.8947
DASH $19.8947 XMR $308.822
XMR $308.822 ETH $2414.77
ETH $2414.77 ADA $0.581065
ADA $0.581065
A hash function is a mathematical transformation that converts arbitrary length data into a fixed length string. Hash functions are a fundamental tool in cryptography and are used in a variety of digital systems including messaging, banking applications and cryptocurrencies. An important aspect of hash functions is that they are unidirectional - input data cannot be converted to output, making them a simple and powerful tool for data protection.
Hash functions play an important role in bitcoin mining and the proof-of-work process. Hash functions ensure the integrity of the blockchain by ensuring that the hash value of each block is unique and immutable. When mining bitcoin, miners compete to find a hash that is smaller than the target value set by the network. To do this, they combine the block header data with a nonce (random number) and run it through a hash function (SHA-256). The result is a fixed-length string of numbers and letters that reflects the contents of the block. Miners try different values of ness until they get a hash that is smaller than the target hash value. Once the desired hash is found, it is sent to the network as proof of work and the miner is rewarded with new bitcoins.
Each attempt to change the data in the block creates another hash value, which the network detects and invalidates. In short, hash functions are critical to the security and integrity of the Bitcoin network, as well as proof-of-work mining. They ensure that each block contains unique and immutable data, and provide the tamper-proof security on which the blockchain is built.
There are several types of hashing algorithms used by individuals and organisations, each with their own unique characteristics. The most common hashing algorithms are Message Digest 5 (MD5), Secure Hash Algorithm 1 (SHA-1), Secure Hash Algorithm 2 (SHA-2), and Secure Hash Algorithm 3 (SHA-3).
Message Digest 5 (MD5) is a cryptographic hash function that produces an output of 128 fixed-size bits, regardless of the size of the input message. MD5 is considered a relatively fast and efficient hashing function, but it has a number of flaws that make it vulnerable to attack. For example, generating different input data can lead to the same MD5 result (called "collision"), which makes it easy for an attacker to create a malicious file that looks like a legitimate one. Because of these vulnerabilities, we no longer recommend using MD5 in new applications that require strong cryptographic security and instead recommend using more secure hash functions such as SHA-256 or SHA-3.
Secure Hash Algorithm 1 (SHA-1) is a hash function that takes input data of arbitrary length and produces a 160-bit (20-byte) hash value called a message digest, usually represented as a 40-bit decimal number. The algorithm was developed by the US Department of Homeland Security in 1995, but has since been abandoned in favour of more secure protocols. SHA-1 transforms user data by breaking the input data into several "n" pieces (448 bits each) and performing 64-bit substitutions to produce a 512-bit result. These 512 bits are processed by the compression function and the result is a 160-bit hash.
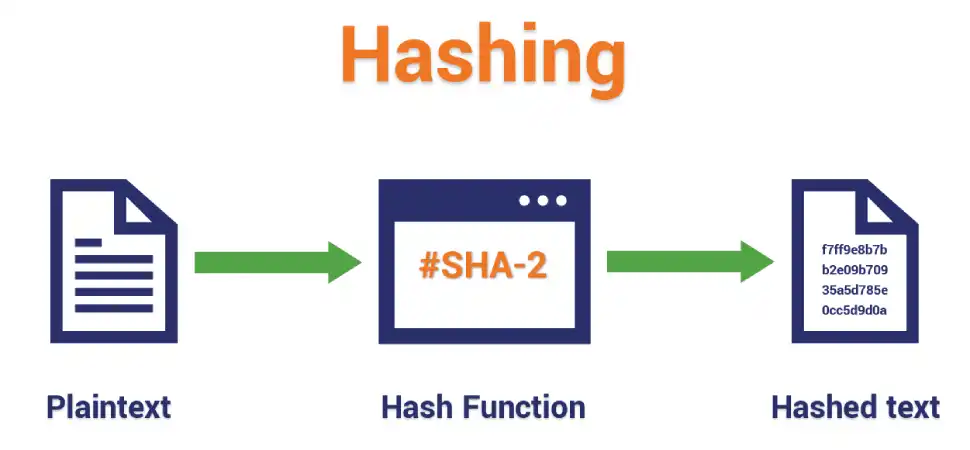
The Secure Hash Algorithm (SHA-2) is a family of cryptographic hash functions including SHA-224, SHA-256, SHA-384, and SHA-512. Like SHA-1, SHA-2 was developed by the U.S. National Security Agency (NSA) and is widely used in a variety of security protocols and applications. SHA-2 uses the same basic structure as SHA-1, but has a larger input and output block size, making it more secure against brute force attacks. SHA-224 and SHA-256 have a word length of 32 bits, while SHA-384 and SHA-512 have 64 bits. SHA-2 works by dividing the input information into fixed-size blocks and processing each block using a number of mathematical operations, including modular addition, bit rotation, and the AND, OR and XOR logic functions. Secure Hash Algorithm 3 (SHA-3)
Secure Hash Algorithm 3 (SHA-3) is the latest version of the Secure Hash Algorithm family of cryptographic hash functions, released in 2015 by the US National Institute of Standards and Technology (NIST) and based on a new framework called the Kekak algorithm, the result of an open competition to develop a new hash standard to replace SHA-2. Like its predecessor, SHA-3 takes as input a message of any length and outputs a fixed-length hash of 224, 256, 384, or 512 bits. SHA-3 uses a mushroom structure that converts input information into algorithmic states and then compresses them to produce an output hash.
The mushroom structure is based on a substitution function that changes the mapping of input bits to output bits. The function is applied iteratively until the input information is completely absorbed into the state. The remaining state is then compressed to create the output hash. One of the major advantages of the SHA-3 algorithm over the SHA-2 algorithm is its resistance to length-increase attacks, which allow an attacker to add information to a hash without revealing the original information. The architecture of SHA-3 is also simpler than SHA-2, making it easier to implement in hardware and software solutions.
SHA-3 is generally considered a secure and efficient cryptographic hash function for digital signatures, key derivation, and data integrity checking. For this reason, keccak-256, a widely used hash function of the SHA-3 family, is widely used in blockchains. The first phase of the Nervos blockchain (Common Knowledge Base, CKB) uses a new SHA-3-based hashing algorithm called Eaglesong.
Hash functions are extremely important for cryptocurrency. Their ability to convert data into unique fixed-length strings is used in many security systems. While hash functions provide strong security, it is important to stay on top of potential vulnerabilities and the constant evolution of cryptographic algorithms. Ultimately, the strength of a cryptocurrency or any other digital system is directly related to the strength of its cryptographic foundations. Hash functions, as one of the fundamental components, play an indispensable role in ensuring the integrity and security of these systems.
0 Comments Found